
IT Security
Every day security threats and security breaches increase and companies struggle to keep up. With LBMC Technology Solutions, you can scale up your security resources without adding staff or a whole security team – saving you time and money, while increasing the security measures for your data.
We will help you set yourself up for success, defending you against the constant emergence of new cyber threats. The needs of networks can vary based on the size and type of organization. Determining how to best protect your assets and educate your employees can present unexpected and unique challenges. If you’re looking for some guidance on how to best secure your networks, just let us know. We can help you get started today with our different types of it security.
Let Us Check To See If You’re Secure
Client Testimonials
Datto
We are a Blue Diamond partner in Datto’s global partner program, the top 2% of all Datto partners worldwide. Datto provides a toolbox of products and services which are tailored to managed service providers and the businesses they serve. These products and services are easy to use. Datto’s industry-leading MSP tools are designed to optimize your business and expand the services you deliver to clients.
Their integrated, scalable, and innovative suite of hardware and software solutions work together to drive success for MSPs of any size. Datto solutions provide backup/disaster recovery protection for on-premise servers, desktops, laptops, and Azure hosted cloud servers. Additionally, they provide protection for Microsoft Dynamics 365 deployments.
Datto Business Continuity and Disaster Recovery Tools:
- SIRIS – High performance business continuity
- ALTO – Business continuity for small business
- Cloud Continuity for PCs – Backup, restore, and protect endpoint data
- Continuity for Microsoft Azure – Data protection for Microsoft Azure
- File Protection – Backup and restore files and folders
- SaaS Protection+ – Secure, protect and restore SaaS applications
Amazon Web Services
LBMC Technology Solutions offers cloud consulting, deployment, migration, and disaster recovery services using Amazon Web Services (AWS). By using cloud computing, organizations can achieve a lower variable cost than they could get on their own. AWS offers a broad set of global computing, cloud security, storage, database, analytic, application, and deployment services.
These services help organizations to lower IT costs, simplify operations, and scale applications quickly.
LBMC Technology Solutions focuses its Infrastructure as a Service (IaaS) expertise on three major areas:
- Replacement of on-premises network infrastructure
- ERP software migration
- Fully Managed Disaster Recovery Services.
Benefits of Amazon Web Services
- Lower IT costs
- Simplify operations
- Quickly scale applications with ease
See How Our Partners Keep Our Clients Safe
Azure
Deploy how you want it, with your choice of tools. Microsoft Azure is a collection of integrated cloud services. IT professionals use these services to build, deploy and manage applications.
These applications are deployed and managed through the Microsoft network of data centers. Enjoy freedom to build and deploy at your leisure, using the tools, frameworks and applications of your choice.
Microsoft Azure has custom cloud solutions especially designed for the healthcare, financial, retail and discrete manufacturing industries. Azure can also connect with SharePoint and Microsoft Dynamics for greater user experience.
Benefits of Azure
- Digital marketing – Connect with digital campaigns that are personalized
- Mobile – Reach customers everywhere, on any device, with a single mobile app
- Cloud Migration – Increase the speed of your digital transformation with cloud migration solutions
- Backup and archive – Protect your data and applications to avoid costly business interruptions
- Disaster Recovery – Protect all major IT systems
WatchGuard

No matter your organization’s size, protect your network infrastructure with a Watchguard next generation firewall.
Safeguard your network with WatchGuard’s award-winning, enterprise-grade network security solutions. Now everyone can have enterprise level protection in one cost-effective, centrally managed solution. With WatchGuard, businesses everywhere can provide a trusted wireless environment for their team members.
The system can be easily configured to give organizations peak performance. Organizations will expect this performance at a desirable price point. With visibility into the entire organization, WatchGuard puts your mind at ease and allows you to focus on building your business.
Benefits of WatchGuard
- Simplicity – Easy and straight-forward to configure, deploy and centrally manage.
- Enterprise-Grade Security – Best-in-class security services without the cost or complexity.
- Visibility – Full network visibility with the power to take action immediately.
- Performance – Fastest UTM performance at all price points.
Secure Wi-Fi
Wi-Fi is Easy. Secure Wi-Fi is the Challenge.
Wi-Fi doesn’t give you a competitive advantage, it offers you a chance to compete. With benefits ranging from increased productivity to improved customer satisfaction, implementing a wireless network for your employees and guests has become the table stakes of doing business, but implementing the wrong technology puts your corporate data, customer privacy, and reputation at risk.
We’ve partnered with WatchGuard Technologies to offer a complete portfolio of wireless solutions that lead the industry in security, visibility, and ease of management.
- Wireless Security: Utilize the industry’s only reliable WIPS technology to block malicious threats ranging from man-in-the-middle attacks to rogue devices. Easily step-up the security of your wireless network by passing all AP-generated traffic through a WatchGuard Firebox security appliance to prevent eavesdropping, malware traps, and data theft.
- Guest Engagement & Analytics: Leverage custom branding and engagement tools to customize the Wi-Fi experience for your guests to improve their browsing experience and the perception of your brand. Once guests are connected, gain access to invaluable demographic, location, and browsing data that can be used to drive a variety of future marketing and sales activities.
- Simplified Management: Experience the easy and intuitive way of managing APs by location and the powerful templates that make administration tasks a breeze through top-down inheritance. Quickly drill down into visual dashboards or automated reports on topics such as Wi-Fi performance, PCI compliance, and airspace risk.
Enabling Wi-Fi is easy, secure Wi-Fi is the challenge. Let us help you connect securely, with confidence.
Threatlocker

Threatlocker – Industry Cybersecurity Leader
- Allowlisting – Only permits approved files to execute and blocks everything else.
- Ringfencing – Allows for granular control over what applications are allowed to do.
- Elevation Control – Run selected applications as a local administrator without making users local administrators.
- Storage Control – Gives you control over all storage device access including USB devices, network shares, and even individual files to help protect data.
- Network Access Control – Protect your endpoints and servers from untrusted devices on you LAN or the internet.
Huntress

Huntress – Add a safety net to your security stack
- Catch hackers who are hiding in plan sight while plotting their next attack.
- Enable quicker ransomware detection and removal to reduce risk.
- Leverage Huntress to extend your front end protection.
- External recon – highlight external attack surfaces and expose easy entry points.
- Managed endpoint detection and response fight against today’s hackers.
- 24/7 human threat hunting.
- Scale you cybersecurity practice with plug-and-play templates
Social Engineering
Threat actors are always thinking of new ways to target individuals and businesses, trying to acquire personal information, login credentials, getting the user to download malicious software or other sensitive information. One of the most common trends today is social engineering. Social engineering is pretending to be someone else to fool a person into revealing sensitive information, passwords, or other information that compromises a target system’s security. Do not become a victim of social engineering by unwittingly giving out information to an unknown person. A skilled social engineer will convince you that a). they are someone they are not and b). there is no harm in giving them the information they are requesting or entering information on malicious websites that appear to be genuine.
Always remember, that social engineering can happen through multiple sources such as email, text messages, and telephone calls. Take these steps to help ensure that you don’t become a victim: Authenticate, Authorize, Make A Phone Call Back, Don’t Be Pressured, Be Alert, Be Polite but Firm, and Report. With the rising amount of ransomware attacks and phishing messages, cyber security has never been more important than it is today.
Another rising trend alongside social engineering is more and more scams on the internet, to learn more read our blog post about common Facebook Marketplace scams.
Social Engineering Tactics
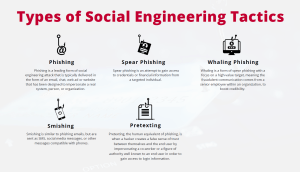
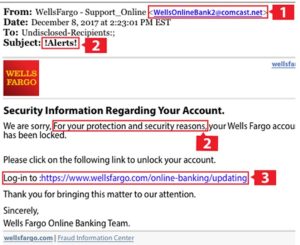
Phishing Indicators Example
Phishing emails are becoming more sophisticated and difficult to distinguish from legitimate emails. By impersonating a reputable company’s communications (with pretexting attacks), these emails tend to use clever and compelling language, such as an urgent need for you to update your information or communicate with you for your security. To spot a phishing email, look for a combination of red flags. In this example, notice:
1. Non-Wells Fargo email address: The email address of the sender does not include the wellsfargo.com domain name, instead using something like “comcast.net”: WellsOnlineBank2@comcast.net.
2. Urgent call to action: The email includes an urgent request in the subject line and message copy, such as “for your protection and for security reasons.” Phishing emails may also contain extra spacing or unusual punctuation in addition to other red flags.
3. Suspicious URL: The email contains a link to a non-Wells Fargo URL, which could be a fraudulent website. If you’re using a laptop or desktop computer, you can check a link’s URL by hovering over it with your cursor, and the URL will show in your browser window.
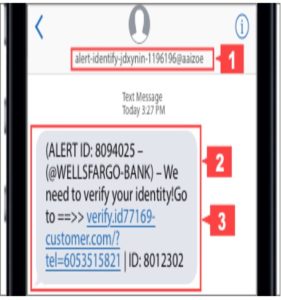
Smishing
How to recognize smishing.
Smishing attacks (SMS Phishing) use similar techniques as phishing emails: a sense of urgency to secure your account or verify your identity, using words like “locked,” “deactivated”, or“ for your protection” to describe your account status. These smishing attacks may prompt you to call a phone number, click on a link, or respond directly with personal or account information. To spot a smishing text, look for a combination of red flags. In this example, notice:
1.Suspicious sender: The text was sent by an unknown phone number, instead of one of Wells Fargo’s official short codes: 93557, 93733, 93729, or 54687.
2. Unusual text treatments: The text message contains a combination of unusual text treatments, including all caps, arrows, ID numbers, and an exclamation point.
3. Unprompted identity request: The request to verify the recipient’s identity was unprompted. Wells Fargo will request to verify your identity via access code only when prompted by an action that you have initiated, such as signing on to online banking or sending money.
To learn more about social engineering and how to protect yourself, check out our podcast.
Make Sure You Don’t Fall Victim To Phishing Attacks
What Makes LBMC Technology Solutions Different?
For over 20 years, LBMC Technology Solutions has been inspiring greatness through technology. We understand how important a reliable technology infrastructure is to your one-of-a-kind business. As your partner, we evaluate your unique business processes and current systems, then identify and apply the most effective solutions.
LBMC Technology Solutions is an award-winning reseller of recognizable industry standard software. If your business needs are beyond what an out-of-the-box software can offer, we will tailor a custom software solution to fit your specific business needs.
Our consultants build connections, nurture innovation, establish ongoing communication, and collaborate with you to architect the best system integration option to help you run your business better. We value our clients’ experience and have made it a critical part of our solutions to ensure we are earning your trust and becoming a long-term partner as your company grows.
Whether you need to supplement or outsource a single function, need an ally you can trust, or are in the market for a comprehensive business partner, LBMC Technology Solutions and our Family of Companies can simply be whatever your business needs us to be.
Contact Us
We’re happy to answer any questions you may have. Please send us an email using the form and one of our professionals will get back to you promptly.
Headquarters – IT Security Nashville, TN:
201 Franklin Road
Brentwood, TN 37027
Phone: 615-377-4600
Office Hours: 8am-5pm, Monday-Friday
IT Security Charlotte, NC
3700 Arco Corporate Drive, Suite 175
Charlotte, NC 28273
704-846-6750
IT Security Knoxville, TN
2095 Lakeside Centre Way
Knoxville, TN 37922
865-691-9000
Inquiries
To better serve you, please review our communication options for the best way to contact us.
If you are seeking general information. Please check out our FAQ page.
If you are interested in more information, complete the form below to have an LBMC Technology Solutions expert contact you.
- In the fast-paced world of sales, staying ahead of the… Read more » The post Revolutionizing Sales: How Leading Brands Harness the Power of Copilot for Success—And You Can Too! appeared first on LBMC Tech.
- In the ever-evolving landscape of customer service, staying ahead of… Read more » The post Elevate Your Copilot for Service with Microsoft Copilot Studio Customization appeared first on LBMC Tech.
- In the ever-evolving landscape of customer service, organizations are constantly… Read more » The post Revolutionizing Customer Service: Microsoft Copilot for Service and Seamless CRM Integrations appeared first on LBMC Tech.
